On 30 October 2020, CNA reported that online shopping platform RedMart, owned by the Lazada Group, suffered a data breach. The stolen database contained the details of 1.1 million customers and was reportedly being sold online. Later that day, Lazada issued a statement confirming that the data breach had happened and sent an email to the affected customers explaining the situation.
In their statement, Lazada claimed that the RedMart database in question was 18-months old and separate from Lazada’s current systems. Lazada also claimed that the stolen customer details contained personal information such as names, addresses, the last 4-digits of credit card numbers, and hashed passwords. Lazada’s statement informed the public that their passwords are “protected by encryption” while advising them to remain “alert for spam emails” and be wary of any “unusual activity”.
A day later, I was able to procure this specific database for 0.087 BTC (worth 1,200 USD or 1,632 SGD then, and worth 3,200 USD or 4,242 SGD at the time of writing). Within minutes of analyzing the database, I found several interesting and worrying elements.
I have written this post to share some of my findings and explain their significance and implication.
Details About the Database
Just some quick tech jargon. The database arrived in the JavaScript Object Notation (JSON) format, containing 1,108,774 entries of RedMart members. From the structure of the file, it can be seen that this is a MongoDB export of the database. We can verify that RedMart uses MongoDB from its GitHub repository here, and their Block71 talk in 2013 about using MongoDB here.
As a MongoDB export, there is no issue importing the database back into a MongoDB environment using `mongoimport`.
Findings – Passwords
Lazada’s statement reassured their customers that their information was well-protected, emphasizing specifically on the safety of users’ passwords. However, the passwords are weakly encrypted. This means a dedicated attacker will be able to recover most passwords, especially in a targeted fashion.
The encryption used is osCommerce MD5 with a salt length of two. The algorithm I believe to be used can be found here. MD5 is generally regarded to be a weak hashing algorithm, even if salt (a mitigation technique) is used. Using HashCat, a password recovery tool, the plaintext version of the passwords could be easily recovered – especially if they were 8 characters and below. As a reminder on password lengths versus entropy (complexity), here is XKCD’s famous strip on Password Strength:
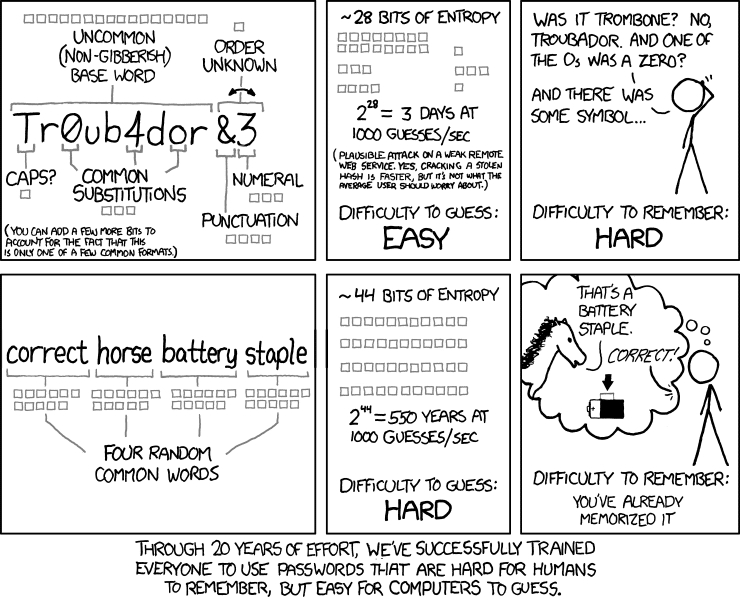
What is confusing is that the database stores both the MD5 (invented 1992) and SHA1 (invented 1995) for each user. It feels like there was an attempt to migrate the hashing algorithm, but the legacy MD5 method continued to be stored. While SHA1 is slightly more secure compared to MD5, the best practice has been to use SHA256 (invented 2001).
Findings – Addresses and Personal Information
Perhaps, more significant is the database’s access to users’ addresses and personal information rather than the perceived access to passwords. Passwords can be changed and with good password hygiene, poses less of an issue should a breach occur. This is especially so if users do not password reuse and/or use a password manager like LastPass. Conversely, addresses and personal information are a lot harder to change.
From the amount of details available in the database – given that RedMart deals with deliveries – it is possible for attackers to glean a lot of information. Not just the contact details such as phone numbers and email addresses which can then be used for phishing, but also more sensitive information such as delivery instructions. For example, there are Government buildings with specific instructions such as who to contact for security clearance and which entrance to take.
By searching based on specific fields (such as the Postal Code), it is possible to find every RedMart user living in the same block. It is also possible to search on a more granular scale and find every user residing in the same household. Have someone’s phone number or email address? If they are in the database, you now have their address.
There may be 1.1 million user accounts, but each user account may have more than one address listed. For example, Person A may have a RedMart account but Person B who lives in the same household does not. Person A may choose to specify Person B as the recipient, perhaps if Person A were not to be home to receive the delivery. By aggregating unique name and address combinations, the total entries come up to approximately 1,275,267.
This potentially allows an attacker to craft a web of data and map members of each household. The ability to find others residing in the same address creates opportunities for phishing attacks or harassment (e.g. “your son is kidnapped, transfer money”).
Findings – Dates
Each account’s entry contains an `updated_at` field, which indicates when the account was last updated. While Lazada’s statement claims that the database was 18-months old (which suggests that it was last updated in approximately June 2019), the latest `updated_at` entry was on 3 September 2020, less than 2-months before the statement.
However, this could be because this database was being run in parallel with the current Lazada database to port over legacy customers. What is clear from this information is that the intrusion to the systems lasted until 3 September 2020 at the earliest.
Findings – Prominent People
There are several prominent people who have been exposed by the database. Turns out, several celebrities and people in the higher echelons of society do their own groceries, after all. I shall not name any for security reasons.
In one case, a certain woman does not have a RedMart account, but her daughter does. The daughter ordered something for her mother and addressed it directly to her. As mentioned earlier, through establishing a web of people, it is then possible to get this woman’s handphone number. As golden as these numbers are, it would be a disaster if it were leaked to the public.
For many of the people I found, I was able to verify that the details are accurate – especially those that used a vanity domain name for their email address.
Findings – Emails
It is not uncommon for people to use their company accounts to sign up for random things online. Continuing the trend from previously discovered data dumps, there are several Government employees who have used their @*.gov.sg (count 436) or @*.moe.edu.sg (count 993) emails, and several students who used their @*.edu.sg (count 5,472) emails.
This poses spear phishing concerns, coupled with the dangers of password reuse. If the password is reused, an attacker can easily gain access to the company email and resources. Having a list of emails and potential passwords, attackers can also try their luck at social engineering specific people within an organization. Using organization emails for personal platforms should be discouraged.
The Attacker
I believe this attack was not a deliberate attempt to steal information from RedMart specifically. The attacker seems to have randomly stumbled upon a vulnerability in a mass scanning attack. The profile of such attackers is to use wild vulnerabilities and scan the web for websites that might be vulnerable, dumping the data they can get and selling it. The attacker appears to have delegated sales to another individual who was selling databases from all over the world, with many above 2 million in entries.
For the price of the database to (initially) be at 1,500 USD, my opinion is that the attacker was not aware of the extent of the database. Likely, the seller felt that 1 million Singaporeans was not a lot of people when the other databases they were selling had millions of entries, albeit international. However, with a sub-6 million population, it does make up a significant percentage.
What’s Next
This data breach is still under investigation by the Personal Data Protection Commission (PDPC), who will probably release a statement of their own findings and penalties.
As society goes digital, cybersecurity becomes imperative to the safety of the general public. Other companies should treat the attack on RedMart as a warning of more cyberattacks to come from various troublemakers and channel more resources into beefing up their cybersecurity.
Where personal identifiable information is at risk, penetration testing and vulnerability assessments should be conducted to ensure the attack surface is minimized. This is important given the amendments to the Personal Data Protection Act (PDPA) passed on 2 November 2020, bringing mandatory notification of data breaches and higher penalty caps.
Consumers should ensure good password hygiene and take care not to leave personal data lying around the Internet. While PDPA in its amended form brings more protections, there are many services worldwide that do not fall under its purview. The Cambridge Analytica scandal proves that even major corporations like Facebook are not infallible.
Cybersecurity is an interesting and fulfilling field, a constant battlefield of good versus bad and everything in-between. Companies, including the Singapore Government’s GovTech, have started bug bounty programs for responsible disclosure. Certainly, an industry to consider.
Timeline
- 30/10/2020: CNA reports on RedMart’s data breach, Lazada Group issues statement
- 31/10/2020: Procurement of the database
- 8/11/2020: Submitted stripped database to Have I Been Pwned’s Troy Hunt
- 10/11/2020: Dataset live on Have I Been Pwned
- 29/1/2021: Published

Leave a Comment